Dynamic Biometric Signature - an Effective Alternative for Electronic Authentication
Keywords:
biometric authentication methods, dynamic biometric signature, electronic signature, authenticationAbstract
The use of dynamic biometric methods for the authentication of people provides significantly greater security than the use of the static ones. The variance of individual dynamic properties of a person, which protects biometric methods against attacks, can be the weak point of these methods at the same time.
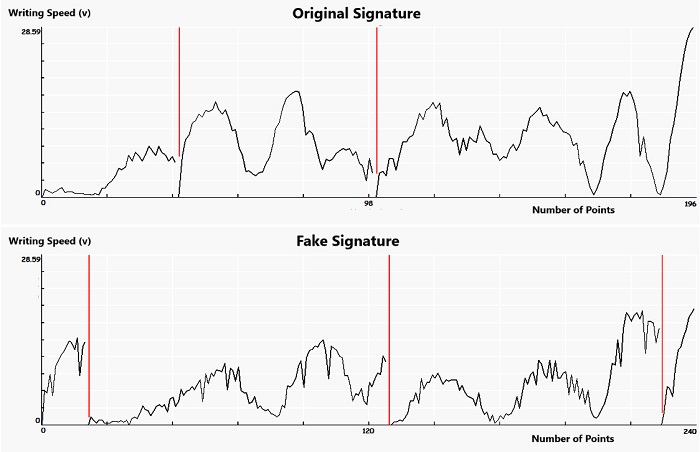
This paper summarizes the results of a long-term research, which shows that a DBS demonstrates practically absolute resistance to forging and that the stability of signatures provided by test subjects in various situations is high. Factors such as alcohol and stress have no influence on signature stability, either. The results of the experiments showed that the handwritten signature obtained through long practice and the consolidation of the dynamic stereotype, is so automated and stored so deep in the human brain, that its involuntary performance also allows other processes to take place in the cerebral cortex. The dynamic stereotype is composed of psychological, anatomical and motor characteristics of each person. It was also proven to be true that the use of different devices did not have a major impact on the stability of signatures, which is of importance in the case of a blanket deployment.
The carried out experiments conclusively showed that the aspects that could have an impact on the stability of a signature did not manifest themselves in such a way that we could not trust these methods even used on commercially available devices. In the conclusion of the paper, the possible directions of research are suggested.
References
V. Smejkal and J. Kodl, “Development trends of electronic authentication,” Proc. of the 42nd Annual Conf. 2008 IEEE International Carnahan Conf. on Security Technology, IEEE Press, October 2008, pp. 1-6.
R. Rak, V. Matyáš, and Z. Říha, “Biometry and identity in forensic and commercial applications,” Grada Publishing, 2008.
M. Gamassi, M. Lazzaroni, M. Misino, V. Piuri, D. Sana, and F. Scotti, “Accuracy and performance of biometric systems,” Proc. of the 21st IEEE Instrumentation and Measurement Technology Conf. (IEEE Cat. No. 04CH37510), IEEE Press, November 2004, pp. 510-515.
V. Smejkal and J. Kodl, “Strong authentication using dynamic biometric signature,” Proc. of 45th Annual 2011 IEEE International Carnahan Conf. on Security Technology (ICCST), IEEE Press, October 2011, pp. 340-344.
ISO/IEC 19794-11:Information technology. Biometric data interchange formats, Part 11: Signature/sign processed dynamic data, IEEE Standard, 2013.
V. Smejkal, J. Kodl, and J. Jr. Kodl, “Implementing trustworthy dynamic biometric signature according to the electronic signature regulations,” Proc. of 47th Annual 2013 IEEE International Carnahan Conf. on Security Technology (ICCST), IEEE Press, October 2014, pp. 165-170.
F. Lacquaniti, C. Terzuolo, and P. Viviani, “The law relating the kinematic and figural aspects of drawing movements,” vol. 54, no. 1-3, pp. 115-130, October 1983.
F. Lacquaniti, “Central representations of human limb movement as revealed by studies of drawing and handwriting,” vol. 12, no. 8, pp. 287-291, 1989.
S. Kandel, J. P. Orliaguet, and P. Viviani, “Perceptual anticipation in handwriting: The role of implicit motor competence,” Perception & Psychophysics, vol. 62, no. 4, pp. 706-716, January 2000.
A. J. Thomassen and H. L. Teulings, “Time, size and shape in handwriting: Exploring spatio-temporal relationships at different levels,” Time, mind, and behavior, Springer Berlin Heidelberg, pp. 253-263, 1985.
Y. Wada and M. Kawato, “A theory for cursive handwriting based on the minimization principle,” Biological Cybernetics, vol. 73, no. 1, pp. 3-13, June 1995.
V. Smejkal and J. Kodl, “Assessment of the authenticity of dynamic biometric signature,” The results of experiments. Proc. of 48th Annual 2014 IEEE International Carnahan Conf. on Security Technology (ICCST), IEEE Press, October 2014, pp. 45-49.
R. Brickenkamp and E. Zillmer, D2-Test of attention, Seattle: Hogrefe & Huber, 1998.
V. Smejkal, J. Kodl, L. Sieger, D. Novák, and J. Schneider, “The dynamic biometric signature. Is the biometric data in the created signature constant?” In Proc. of 49th Annual 2015 IEEE International Carnahan Conf. on Security Technology (ICCST), IEEE Press, September 2015, pp. 385-390.
E. Ambrozová, J. Koleňák, D. Ullrich, V. Okorný, and D. Cibulka, “X-tream index and multi-parameter personality dimension for managers cognition and decision-making in the modern corporate environment,” Global Journal for Research Analysis, vol. 4, no. 3, pp. 1-7, 2015.
R. Tolosana, R. Vera-rodriguez, J. Ortega-Garcia, and J. Fierrez, “Increasing the robustness of biometric templates for dynamic signature biometric systems,” In Proc. of 49th Annual IEEE International Carnahan Conf. on Security Technology (ICCST), IEEE Press, September 2015, pp. 229-234.
J. KODL Jr., “Mechanisms of human arm motion planning in the presence of multiple solutions,” Imperial College, 2010.
A. Rattani and A. Ross, “Automatic adaptation of fingerprint liveness detector to new spoof materials,” 2014 IEEE International Joint Conf. on Biometrics (IJCB), IEEE Press, December 2014, pp. 1-8.
A. AL-AJLAN, “Survey on fingerprint liveness detection,” 2013 International Workshop on Biometrics and Forensics (IWBF), Lisbon, IEEE Press, April 2013, pp. 1-5.
L. Ghiani, D. Yambay, V. Mura, S. Tocco, G. L. Marcialis, F. Roli, and S. Schuckers, “Livdet 2013 fingerprint liveness detection competition 2013,” 2013 International Conf. on Biometrics (ICB), IEEE Press, September 2013, pp. 1-6.
M. Drahanský, O. Kanich, and E. Březinová, “Challenges for fingerprint recognition-spoofing, skin diseases and environmental effects,” In Handbook of Biometrics for Forensic Science, Advances in Computer Vision and Pattern Recognition, 2017.
A. Greenberg, “We tried really hard to beat face id-and failed (so far),” https://www.wired.com/story/tried-to-beat-face-id-and-failed-so-far/.
The future is here: iPhone X. Apple Inc. Press release, September 2017.
A. Greenberg, “How secure is the iphone x's faceid? Here's what we know,” https://www.wired.com/story/iphone-x-faceid-security/.
G. W. Snedecor and W. G. Cochran, “Statistical methods. eighth edition,” Iowa State University Press, 1989.
W. G. Cochran and G. M. Cox, Experimental & designs, 2nd ed. New York: John Wiley and Sons, 1957.
H. Scheffé, The Analysis & Variance, New York: John Wiley and Sons, 1999.
V. Smejkal, J. Kodl, L. Sieger, F. Hortai, and P. Tesař, “Stability of a dynamic biometric signature created on various devices,” IEEE Press, December 2017.
Published
How to Cite
Issue
Section
License
Submission of a manuscript implies: that the work described has not been published before that it is not under consideration for publication elsewhere; that if and when the manuscript is accepted for publication. Authors can retain copyright in their articles with no restrictions. is accepted for publication. Authors can retain copyright of their article with no restrictions.
Since Jan. 01, 2019, AITI will publish new articles with Creative Commons Attribution Non-Commercial License, under The Creative Commons Attribution Non-Commercial 4.0 International (CC BY-NC 4.0) License.
The Creative Commons Attribution Non-Commercial (CC-BY-NC) License permits use, distribution and reproduction in any medium, provided the original work is properly cited and is not used for commercial purposes.



