Security Enhancement in Image Watermarking Using Combined Medium Sub-Band Wavelet Approach for Copyright Protection
DOI:
https://doi.org/10.46604/peti.2021.5316Keywords:
copyright protection, image sharing, sub-band fusion, wavelet transform, watermarkingAbstract
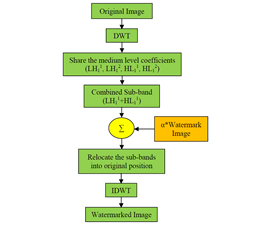
Watermarking in multimedia content has secured attractive approaches in research society since nowadays the transmission of digital content in wireless medium has been enormous. Along with the distribution of digital content, it is important to claim ownership. A non-blind detection technique is proposed in this paper. First, an original image undergoes the wavelet decomposition such as LL1, LH1, HL1, and HH2. Afterward, the medium level sub-band coefficients of the image are subject to the comfortable shares for merging. Next, one of the shares from the LH1 band is merging with another one of the shares in HL1 band. In this stage, the copyright mark is fetched into the merged sub-band coefficients. Finally, an inverse wavelet transform is applied to receive the watermarked image. To prove the authentication, the original image and the watermarked image undergo the same operation and acquire copyright information. Experimental results achieve that the proposed approach can withstand various image processing attacks.
References
Q. Li and I. J. Cox, “Using Perceptual Models to Improve Fidelity and Provide Resistance to Valumetric Scaling for Quantization Index Modulation Watermarking,” IEEE Transaction on Information Forensics and Security, vol. 2, no. 2, pp. 127-139, June 2007.
A. Piva, T. Bianchi, and A. De Rosa, “Secure Client-Side ST-DM Watermark Embedding,” IEEE Transactions on Information Forensics and Security, vol. 5, no. 1, pp. 13-26, March 2010.
A. Piva, F. Bartolini, and M. Barni, “Managing Copyright in Open Networks,” IEEE Internet Computing, vol. 6, no. 3, pp. 18-26, May-June 2002.
B. Sridhar, “A Wavelet Based Watermarking in Video Using Layer Fusion Technique,” Pattern Recognition and Image Analysis, vol. 28, no. 3, pp. 537-545, July 2018.
V. M. Potdar, S. Han, and E. Chang, “A Survey of Digital Image Watermarking Techniques,” 3rd IEEE International Conference on Industrial Informatics (INDIN), August 2005, pp. 709-713.
Y. Wang, J. F. Doherty, and R. E. Van Dyck, “A Wavelet Based Watermarking Algorithm for Ownership Verification of Digital Image,” IEEE Transactions on Image Processing, vol. 11, no. 2, pp. 77-88, February 2002.
S. Dey, A. Abraham, and S. Sanyal, “An LSB Data Hiding Technique Using Natural Number Decomposition,” Third International Conference on Intelligent Information Hiding and Multimedia Signal Processing, November 2007, pp. 473-476.
G. Ren, C. Zhang, and X. Yang, “Blind Mesh Watermarking Based on the Featured Points in the Frequency Domain,” Second International Workshop on Knowledge Discovery and Data Mining, January 2009, pp. 701-704.
N. Hubballi and D. P. Kanyakumari, “Novel DCT Based Watermarking Scheme for Digital Image,” International Journal of Recent Trends in Engineering, vol. 1, no. 1, pp. 430-433, 2009.
B. Sridhar, “Cross-Layered Embedding of Watermark on Image for High Authentication,” Pattern Recognition and Image Analysis, vol. 29, no. 1, pp. 194-199, January 2019.
B. Sridhar, “A Wavelet Based Watermarking Approach in Concatenated Square Block Image for High Security,” Journal of Automation, Mobile Robotics and Intelligent Systems, vol. 12, no. 3, pp. 68-72, December 2018.
H. J. Lin, C. W. Lu, and C. M. Chiang, “DWT-Based Watermarking Technique Associated with Embedding Rule,” 10th WSEAS International Conference on Signal Processing, Computational Geometry and Artificial Vision, August 2010, pp. 23-28.
J. N. Ellinas, “A Robust Wavelet-Based Watermarking Algorithm Using Edge Detection,” World Academy of Science, Engineering and Technology, vol. 1, no. 10, January 2007.
A. A. Mohammed and H. M. Sidqi, “Robust Image Watermarking Scheme Based on Wavelet Technique,” International Journal of Computer Science and Security (IJCSS), vol. 5, no. 4, pp. 394-404, September-October 2011.
P. Surekha and S. Sumathi, “Implementation of Genetic Algorithm for a DWT Based Image Watermarking Scheme,” ICTACT Journal on Soft Computing: Special Issue on Fuzzy in Industrial and Process Automation, vol. 2, no. 1, pp. 244-252, July 2011.
H. A. Abdallah, M. M. Hadhoud, A. A. Shaalan, and F. E. Abd El-samie, “Blind Wavelet-Based Image Watermarking,” International Journal of Signal Processing, Image Processing and Pattern Recognition, vol. 4, no. 1, pp. 15-28, 2011.
S. Sood and A. Goyal, “Watermarking Relational Databases Using Genetic Algorithm and Bacterial Foraging Algorithm,” International Journal of Information and Computation Technology, vol. 4, no. 17, pp. 1877-1884, 2014.
A. N. Yahya, H. A. Jalab, A. Wahid, and R. M. Noor, “Robust Watermarking Algorithm for Digital Images Using Discrete Wavelet and Probabilistic Neural Network,” Journal of King Saud University—Computer and Information Sciences, vol. 27, no. 4, pp. 393-401, October 2015.
P. Tanwar and M. Khurana, “Improved PSNR and NC in Digital Image Watermarking Using RDWT and SVD,” International Journal of Advanced Research in Computer Science and Software Engineering Research, vol. 6, no. 5, pp. 955-959, May 2016.
Published
How to Cite
Issue
Section
License
Submission of a manuscript implies: that the work described has not been published before that it is not under consideration for publication elsewhere; that if and when the manuscript is accepted for publication. Authors can retain copyright of their article with no restrictions. Also, author can post the final, peer-reviewed manuscript version (postprint) to any repository or website.

Since Oct. 01, 2015, PETI will publish new articles with Creative Commons Attribution Non-Commercial License, under The Creative Commons Attribution Non-Commercial 4.0 International (CC BY-NC 4.0) License.
The Creative Commons Attribution Non-Commercial (CC-BY-NC) License permits use, distribution and reproduction in any medium, provided the original work is properly cited and is not used for commercial purposes







