A Novel Data Transmission Model Using Hybrid Encryption Scheme for Preserving Data Integrity
DOI:
https://doi.org/10.46604/aiti.2024.14114Keywords:
hybrid encryption, cryptographic security, RSA, ChaCha20-Poly1305, data shufflingAbstract
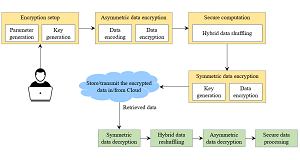
The objective of the study is to introduce a novel hybrid encryption scheme, combining both symmetric and asymmetric encryptions with a data shuffling mechanism, to enhance data obfuscation and encryption security. The approach uses RSA for asymmetric encryption and ChaCha20-Poly1305 for symmetric encryption. To increase the complexity, an additional phase involves reorganizing the RSA-encrypted data blocks. Furthermore, symmetric key generation using the key derivation function is employed to generate the key for symmetric encryption through an asymmetric private key. Decryption entails reversing these procedures. This model significantly enhances security through an additional shuffling step, measured by performance metrics like encryption and decryption times, throughput rate, and the avalanche effect. The method, despite increasing execution time compared to symmetric models, yields comparable results for asymmetric models and ensures robustness. The proposed method outperforms traditional methods regarding resistance to cryptanalytic attacks, including chosen-plaintext and pattern analysis attacks.
References
S. Kolasani, “Innovations in Digital, Enterprise, Cloud, Data Transformation, and Organizational Change Management Using Agile, Lean, and Data-Driven Methodologies,” International Journal of Machine Learning and Artificial Intelligence, vol. 4, no. 4, pp. 1-18, 2023.
A. Saravanan and S. Sathya Bama, “A Review on Cyber Security and the Fifth Generation Cyberattacks,” Oriental Journal of Computer Science and Technology, vol. 12, no. 2, pp. 50-56, 2019.
A. Saravanan, S. Sathya Bama, S. Kadry, and L. K. Ramasamy, “A New Framework to Alleviate DDoS Vulnerabilities in Cloud Computing,” International Journal of Electrical and Computer Engineering, vol. 9, no. 5, pp. 4163-4175, 2019.
A. Saravanan and S. Sathya Bama, “CloudSec (3FA): A Multifactor With Dynamic Click Colour-Based Dynamic Authentication for Securing Cloud Environment,” International Journal of Information and Computer Security, vol. 20, no. 3-4, pp. 269-294, 2023.
Q. Zhang, “An Overview and Analysis of Hybrid Encryption: The Combination of Symmetric Encryption and Asymmetric Encryption,” 2nd International Conference on Computing and Data Science, pp. 616-622, 2021.
A. E. Adeniyi, K. M. Abiodun, J. B. Awotunde, M. Olagunju, O. S. Ojo, and N. P. Edet, “Implementation of a Block Cipher Algorithm for Medical Information Security on Cloud Environment: Using Modified Advanced Encryption Standard Approach,” Multimedia Tools and Applications, vol. 82, no. 13, pp. 20537-20551, 2023.
K. K. Reddy, A. R. Chadha, P. S. Nikhil, and S. Sountharrajan, “Hybrid Cryptography Techniques for Data Security in Cloud Computing,” IEEE International Conference on Computing, Power and Communication Technologies, pp. 1836-1842, 2024.
B. P. Kavin and S. Ganapathy, “A New Digital Signature Algorithm for Ensuring the Data Integrity in Cloud Using Elliptic Curves,” International Arab Journal of Information Technology, vol. 18, no. 2, pp. 180-190, 2021.
Y. Alghofaili, A. Albattah, N. Alrajeh, M. A. Rassam, and B. A. S. Al-Rimy, “Secure Cloud Infrastructure: A Survey on Issues, Current Solutions, and Open Challenges,” Applied Sciences, vol. 11, no. 19, article no. 9005, 2021.
A. Orobosade, T. A. Favour-Bethy, A. B. Kayode, and A. J. Gabriel, “Cloud Application Security Using Hybrid Encryption,” Communications on Applied Electronics, vol. 7, no. 33, pp. 25-31, 2020.
S. Arumugam, “An Effective Hybrid Encryption Model using Biometric Key for Ensuring Data Security,” International Arab Journal of Information Technology, vol. 20, no. 5, pp. 796-807, 2023
R. Akter, M. A. R. Khan, F. Rahman, S. J. Soheli, and N. J. Suha, “RSA and AES Based Hybrid Encryption Technique for Enhancing Data Security in Cloud Computing,” International Journal of Computational and Applied Mathematics & Computer Science, vol. 3, pp. 60-71, 2023.
R. Nadaf, N. B. Sumangala, M. Mandi, and A. Konnur, “Symmetric and Asymmetric Cryptographic Approach Based Security Protocol for Key Exchange,” International Conference on Applied Intelligence and Sustainable Computing, pp. 1-6, 2023.
S. Rehman, N. Talat Bajwa, M. A. Shah, A. O. Aseeri, and A. Anjum, “Hybrid AES-ECC Model for the Security of Data Over Cloud Storage,” Electronics, vol. 10, no. 21, article no. 2673, 2021.
D. Kumar Shukla, O. Khalaf, R. Vallabhaneni, S. Kumar Srivastava, and S. Algburi, “A Three-Phase Hybrid Cryptography Algorithm: Utilized in Public Sensor Network for Data Security With an Enhancement of Hashing Algorithm,” International Journal of Computing and Digital Systems, vol. 15, no. 1, pp. 1-13, 2024.
A. Dutta, R. Bose, S. Roy, and S. Sutradhar, “Hybrid Encryption Technique to Enhance Security of Health Data in Cloud Environment,” Archives of Pharmacy Practice, vol. 14, no. 3, pp. 41-47, 2023.
S. K. Maddila and N. Vadlamani, “A Novel Efficient Hybrid Encryption Algorithm Based on Twofish and Key Generation Using Optimization for Ensuring Data Security in Cloud,” Journal of Information & Knowledge Management, vol. 23, no. 01, article no. 2350062, 2024.
A. Almalawi, S. Hassan, A. Fahad, and A. I. Khan, “A Hybrid Cryptographic Mechanism for Secure Data Transmission in Edge AI Networks,” International Journal of Computational Intelligence Systems, vol. 17, no. 1, article no. 24, 2024.
Anjana and A. Singh, “An Enhanced Three Layer Cryptographic Algorithm for Cloud Information Security,” International Journal of Intelligent Systems and Applications in Engineering, vol. 12, no. 17s, pp. 615-627, 2024.
H. Abroshan, “A Hybrid Encryption Solution to Improve Cloud Computing Security Using Symmetric and Asymmetric Cryptography Algorithms,” International Journal of Advanced Computer Science and Applications, vol. 12, no. 6, pp. 31-37, 2021.
Published
How to Cite
Issue
Section
License
Copyright (c) 2024 Riyaz Fathima Abdul, Saravanan Arumugam

This work is licensed under a Creative Commons Attribution-NonCommercial 4.0 International License.
Submission of a manuscript implies: that the work described has not been published before that it is not under consideration for publication elsewhere; that if and when the manuscript is accepted for publication. Authors can retain copyright in their articles with no restrictions. is accepted for publication. Authors can retain copyright of their article with no restrictions.
Since Jan. 01, 2019, AITI will publish new articles with Creative Commons Attribution Non-Commercial License, under The Creative Commons Attribution Non-Commercial 4.0 International (CC BY-NC 4.0) License.
The Creative Commons Attribution Non-Commercial (CC-BY-NC) License permits use, distribution and reproduction in any medium, provided the original work is properly cited and is not used for commercial purposes.







