Multicriteria Decision Analysis on Information Security Policy: A Prioritization Approach
DOI:
https://doi.org/10.46604/aiti.2021.5476Keywords:
analytic hierarchy process, evaluation process, information security, prioritizationAbstract
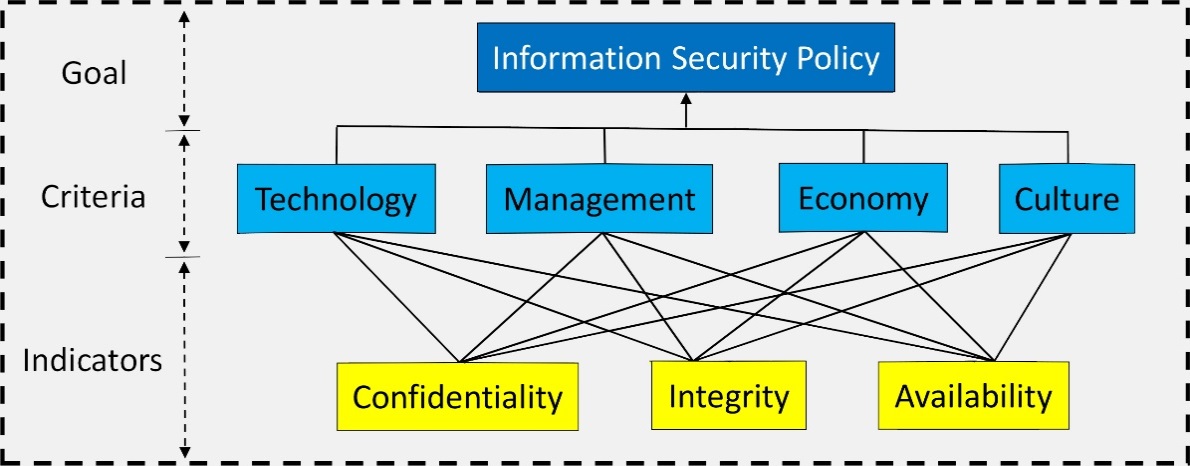
Security is the most serious concern in the digital environment. To provide a sound and firm security policy, a multi-holistic approach must be considered when making strategic decisions. Thus, the objective of this study was to evaluate the information security (IS) and decision making of Davao Oriental State University (DORSU) using the analytic hierarchy process (AHP) approach. The four aspects of IS, namely, the technology, management, economy, and culture were used with the three IS components consisting of confidentiality, integrity, and availability to implement the AHP. The results showed that the technology and management have higher significant values than the economic and cultural aspects. Meanwhile, for the IS components, the integrity signifies the highest priority followed by confidentiality, lastly, and availability. These results emphasize an imbalance in implementing IS policy, which must be addressed to ensure that the data integrity, confidentiality, and availability are balanced, particularly during the information exchange transactions.
References
R. Anderson, “Why Information Security is Hard: An Economic Perspective,” Proc. Annual Computer Security Applications Conference, December 2001, pp. 358-365.
J. P. Laudon and K. C. Laudon, Management Information Systems: Managing the Digital Firm, 12th ed. England: Pearson Education Limited, 2012.
S. Shackleford, A. Proia, B. Martell, and A. Craig, “Toward a Global Cybersecurity Standard of Care? Exploring the Implications of the 2014 NIST Cybersecurity,” Texas International Law Journal, no. 291, 2015.
Y. P. Surwade and H. J. Patil, “Information Security,” E-Journal of Library and Information Science, pp. 458-466, January 2019.
A. Singh, A. Vaish, and P. K. Keserwani, “Information Security: Components and Techniques,” International Journal of Advanced Research in Computer Science and Software Engineering, vol. 4, no. 1, pp. 1072-1077, January 2014.
A. R. Otero, Information Technology Control and Audit, 5th ed. New York: Auerbach Publications, 2018.
S. Mishra and G. Dhillon, “Defining Internal Control Objectives for Information Systems Security: A Value Focused Assessment,” Proc. European Conference on Information Systems (ECIS 2008), January 2008.
D. La Marca, “Aspects of IT Security,” https://www.mediabuzz.com.sg/research-aug-13/aspects-of-it-security, December 02, 2019.
K. Brauer, “Authentication and Security Aspects in an International Multi-User Network,” Turku University of Applied Sciences, Thesis, May 17, 2011.
H. Moghaddasi, S. Sajjadi, and M. Kamkarhaghighi, “Reasons in Support of Data Security and Data Security Management as Two Independent Concepts: A New Model,” The Open Medical Informatics Journal, vol. 10, pp.4-10, October, 2016.
A. Alhogail and A. Mirza, “Information Security Culture: A Definition and a Literature Review,” World Congress on Computer Applications and Information Systems, IEEE Press, October 2014.
L. Xu, Y. Li, and J. Fu, “Cybersecurity Investment Allocation for a Multi-Branch Firm: Modeling and Optimization,” Mathematics, vol. 7, no. 7, pp. 1-20, July 2019.
I. Syamsuddin, “Strategic Information Security Decision Making with Analytic Hierarchy Process,” International Research Journal of Applied Basic Sciences, vol. 2, no. 11, pp. 426-432, 2011.
I. Syamsuddin and J. Hwang, “The Application of AHP to Evaluate Information Security Policy Decision,” International Journal of Simulation: Systems, Science and Technology, vol. 10, pp. 46-50, 2014.
L. A. Gordon and M. P. Loeb, “The Economics of Information Security Investment,” ACM Transactions on Information and System Security, vol. 5, no. 4, pp. 438-457, November 2002.
G. Dhillon, Principles of Information Systems Security: Texts and Cases, 1st ed., John Wiley & Sons, 2007.
L. Ngo, W. Zhou, and M. Warren, “Understanding Transition towards Information Security Culture Change,” Australian Information Security Management Conference, June 2014, pp. 67-73.
R. Dunham, “Information Security Policies: Why They Are Important to Your Organization,” https://linfordco.com/blog/information-security-policies/, May 5, 2020.
T. L. Saaty, The Analytic Hierarchy Process: Planning, Priority Setting Resource Allocation, New York: Mc Graw-Hill, 1980.
T. L. Saaty, “A Scaling Method for Priorities in Hierarchical Structures,” Journal of Mathematical Psychology, vol. 15, no. 3, pp. 234-281, June 1977.
J. S. Cabrera and H. S. Lee, “Impacts of Climate Change on Flood-Prone Areas in Davao Oriental, Philippines,” Water vol. 10, no. 7, 893, July 2018.
T. L. Saaty, Decision Making for Leaders: The Analytic Hierarchy Process for Decisions in a Complex World, 3rd ed. Pittsburgh: RWS Publications, 2012.
Z. Milanović, “Information-Security Culture of Youth in Serbia,” FBIM Transactions, vol. 7, no. 1, pp. 110-118, April 2019.
T. Schlienger and S. Teufel, “Analyzing Information Security Culture: Increased Trust by an Appropriate Information Security Culture,” International Workshop on Database and Expert Systems Applications, September 2003, pp. 405-409.
L. V. Astakhova, “The Concept of the Information-Security Culture,” Scientific and Technical Information Processing, vol. 41, no. 1, pp. 22-28, April 2014.
J. Hwang and I. Syamsuddin, “Information Security Policy Decision Making: An Analytical Hierarchy Process Approach,” Third Asia International Conference on Modeling & Simulation, May 2009, pp. 158-163.
Published
How to Cite
Issue
Section
License
Submission of a manuscript implies: that the work described has not been published before that it is not under consideration for publication elsewhere; that if and when the manuscript is accepted for publication. Authors can retain copyright in their articles with no restrictions. is accepted for publication. Authors can retain copyright of their article with no restrictions.
Since Jan. 01, 2019, AITI will publish new articles with Creative Commons Attribution Non-Commercial License, under The Creative Commons Attribution Non-Commercial 4.0 International (CC BY-NC 4.0) License.
The Creative Commons Attribution Non-Commercial (CC-BY-NC) License permits use, distribution and reproduction in any medium, provided the original work is properly cited and is not used for commercial purposes.







