Securing Ad Hoc Wireless Sensor Networks under Byzantine Attacks by Implementing Non-Cryptographic Methods
Keywords:
Byzantine attacks, cluster based wireless sensor network, advanced node, gray hole, black hole, non-cryptographic algorithmAbstract
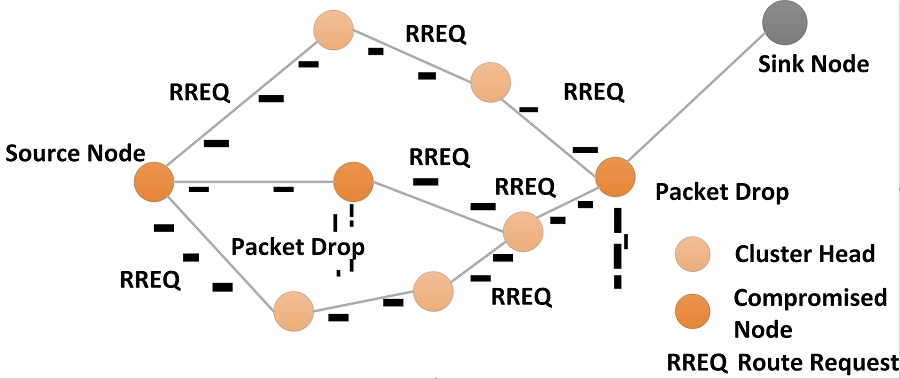
Ad Hoc wireless sensor network (WSN) is a collection of nodes that do not need to rely on predefined infrastructure to keep the network connected. The level of security and performance are always somehow related to each other, therefore due to limited resources in WSN, cryptographic methods for securing the network against attacks is not feasible. Byzantine attacks disrupt the communication between nodes in the network without regard to its own resource consumption. This paper discusses the performance of cluster based WSN comparing LEACH with Advanced node based clusters under byzantine attacks. This paper also proposes an algorithm for detection and isolation of the compromised nodes to mitigate the attacks by non-cryptographic means. The throughput increases after using the algorithm for isolation of the malicious nodes, 33% in case of Gray Hole attack and 62% in case of Black Hole attack.
References
A. Perrig, J. Stankovic, and D. Wager, “Security in wireless sensor networks,” Communication of the ACM, vol. 47, no. 6, pp. 53-57, June 2004.
D. Estrin, R. Govindan, and J. Heidemann, S. Kumar, “Next century challenges: scalable coordination in sensor networks,” Proc. ACM International Conf. Mobile Computing and Networking, ACM Press, 1999, pp. 263-270.
Y. Yu, B. Krishnamachari, V. K. Prasanna, “Ener-gy-latency tradeoffs for data gathering in wireless sensor networks,” Proc. IEEE Computer and Communication Societies, IEEE Press, 2004.
S. E. Khediri, N. Nasri, A. Wei, and A. Kachouri, “A new approach for clustering in wireless sensors networks based on LEACH,” Procedia Computer Science, vol. 32, pp. 1180-1185, 2014.
S. A. Sofi and R. Naaz, “Energy efficient routing pro-tocol for structured deployment of wireless sensor networks,” International Conf. Next Generation Networks, IET Press, September 2010, p. 10.
S. Sofi, E. Malik, R. Baba, H. Baba, and R. Mir, “Analysis of byzantine attacks in ad hoc networks and their mitigation,” International Conf. Computing and Information Technology, February 2012, pp.794-799.
W. Li and A. Joshi, “Security issues in mobile ad hoc networks - a survey,” https://pdfs.semanticscholar.org/b221/99c61df5445836c5f1bbd0ea6f02dabefd6b.pdf, 2007.
Y. C. Hu, A. Perrig, and D. B. Johnson, “Rushing attacks in wireless ad hoc network routing protocols,” Proc. 2nd ACM workshop on Wireless security, ACM Press, 2003, pp. 30-40.
C. Karlof and D. Wagner, “Secure routing in wireless sensor networks: attacks and countermeasures,” Ad hoc networks, vol. 1, no. 2, pp. 293-315, 2003.
S. Marti, T. J. Giuli, K. Lai, and M. Baker, “Mitigating routing misbehavior in mobile ad-hoc networks,” Proc. 6th Annual International Conf. Mobile Computing and Networking, pp. 255-265, August 2000.
H. Li, K. Li, W. Qu, and I. Stojmenovic, “Secure and energy efficient data aggregation with malicious aggregator identification in wireless sensor networks,” Future Generation Computer Systems, vol. 37, pp. 108-116, 2014.
Y. Zhao, Y. Zhang, Z. Qin, and T. Znati, “A co-commitment based secure data collection scheme for tiered wireless sensor networks,” Journal of Systems Architecture , vol. 57, no. 6, pp. 655-662, 2011.
Manju, S. Chand, and B. Kumar, “Improved-coverage preserving clustering protocol in wireless sensor networks,” International Journal of Engineering and Technology of Innovation, vol. 6, no. 1, pp. 16-29, 2016.
R. Duche and N. Sawade, “Energy efficient fault tolerant sensor node failure detection in WSNS,” International Journal of Engineering and Technology of Innovation, vol. 6, no. 3, pp. 190-210, 2016.
M. Abdelhakim, L. E. Lightfoot, J. Ren, and T. Li, “Distributed detection in mobile access wireless sensor networks under byzantine attacks,” IEEE Transactions on Parallel and Distributed Systems, vol. 25, no. 4, pp. 950-959, April 2014.
M. Young and R. Boutaba, “Overcoming adversaries in sensor networks: a survey of theoritical models and algorithm approaches for tolerating malicious interferences,” IEEE Communications Survey and Tutorials, vol. 13, no. 4, 2011.
Published
How to Cite
Issue
Section
License
Submission of a manuscript implies: that the work described has not been published before that it is not under consideration for publication elsewhere; that if and when the manuscript is accepted for publication. Authors can retain copyright in their articles with no restrictions. is accepted for publication. Authors can retain copyright of their article with no restrictions.
Since Jan. 01, 2019, AITI will publish new articles with Creative Commons Attribution Non-Commercial License, under The Creative Commons Attribution Non-Commercial 4.0 International (CC BY-NC 4.0) License.
The Creative Commons Attribution Non-Commercial (CC-BY-NC) License permits use, distribution and reproduction in any medium, provided the original work is properly cited and is not used for commercial purposes.



