Partitioning-Based Data Sharing Approach for Data Integrity Verification in Distributed Fog Computing
DOI:
https://doi.org/10.46604/ijeti.2023.10685Keywords:
fog computing, data integrity, cloud computing, fuzzy clustering, dynamic keyAbstract
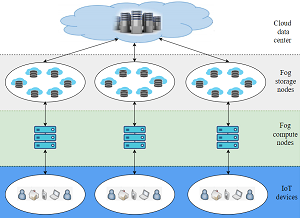
With the increasing popularity of the internet of things (IoT), fog computing has emerged as a unique cutting-edge approach along with cloud computing. This study proposes an approach for data integrity verification in fog computing that does not require metadata stored on the user side and can handle big data efficiently. In the proposed work, fuzzy clustering is used to cluster IoT data; dynamic keys are used to encrypt the clusters; and dynamic permutation is used to distribute encrypted clusters among fog nodes. During the process of data retrieval, fuzzy clustering and message authentication code (MAC) are used to verify the data integrity. Fuzzy clustering and dynamic primitives make the proposed approach more secure. The security analysis indicates that the proposed approach is resilient to various security attacks. Moreover, the performance analysis shows that the computation time of the proposed work is 50 times better than the existing tag regeneration scheme.
References
C. Wang, S. S. M. Chow, Q. Wang, K. Ren, and W. Lou, “Privacy-Preserving Public Auditing for Secure Cloud Storage,” IEEE Transactions on Computers, vol. 62, no. 2, pp. 362-375, February 2013.
X. Zhang and W. Si, “Efficient Auditing Scheme for Secure Data Storage in Fog-to-Cloud Computing,” IEEE Access, vol. 9, pp. 37951-37960, 2021.
H. Noura, O. Salman, A. Chehab, and R. Couturier, “Preserving Data Security in Distributed Fog Computing,” Ad Hoc Networks, vol. 94, article no. 101937, November 2019.
G. Ateniese, R. Burns, R. Curtmola, J. Herring, L. Kissner, Z. Peterson, et al., “Provable Data Possession at Untrusted Stores,” Proceedings of the 14th ACM Conference on Computer and Communications Security, pp. 598-609, October 2007.
Q. Wang, C. Wang, K. Ren, W. Lou, and J. Li, “Enabling Public Auditability and Data Dynamics for Storage Security in Cloud Computing,” IEEE Transactions on Parallel and Distributed Systems, vol. 22, no. 5, pp. 847-859, May 2011.
B. Shao, G. Bian, Y. Wang, S. Su, and C. Guo, “Dynamic Data Integrity Auditing Method Supporting Privacy Protection in Vehicular Cloud Environment,” IEEE Access, vol. 6, pp. 43785-43797, 2018.
A. Fu, Y. Li, S. Yu, Y. Yu, and G. Zhang, “DIPOR: An IDA-Based Dynamic Proof of Retrievability Scheme for Cloud Storage Systems,” Journal of Network and Computer Applications, vol. 104, pp. 97-106, February 2018.
H. Tian, Y. Chen, C. C. Chang, H. Jiang, Y. Huang, Y. Chen, et al., “Dynamic-Hash-Table Based Public Auditing for Secure Cloud Storage,” IEEE Transactions on Services Computing, vol. 10, no. 5, pp. 701-714, September-October 2017.
J. Shen, J. Shen, X. Chen, X. Huang, and W. Susilo, “An Efficient Public Auditing Protocol with Novel Dynamic Structure for Cloud Data,” IEEE Transactions on Information Forensics and Security, vol. 12, no. 10, pp. 2402-2415, October 2017.
W. I. Khedr, H. M. Khater, and E. R. Mohamed, “Cryptographic Accumulator-Based Scheme for Critical Data Integrity Verification in Cloud Storage,” IEEE Access, vol. 7, pp. 65635-65651, 2019.
Y. Guan, J. Shao, G. Wei, and M. Xie, “Data Security and Privacy in Fog Computing,” IEEE Network, vol. 32, no. 5, pp. 106-111, September-October 2018.
M. A. M. Ahsan, I. Ali, M. Imran, M. Y. I. B. Idris, S. Khan, and A. Khan, “A Fog-Centric Secure Cloud Storage Scheme,” IEEE Transactions on Sustainable Computing, vol. 7, no. 2, pp. 250-262, April-June 2022.
T. Wang, J. Zhou, M. Huang, M. Z. A. Bhuiyan, A. Liu, W. Xu, et al., “Fog-Based Storage Technology to Fight with Cyber Threat,” Future Generation Computer Systems, vol. 83, pp. 208-218, June 2018.
S. Basudan, X. Lin, and K. Sankaranarayanan, “A Privacy-Preserving Vehicular Crowdsensing-Based Road Surface Condition Monitoring System Using Fog Computing,” IEEE Internet of Things Journal, vol. 4, no. 3, pp. 772-782, June 2017.
B. Wang, Z. Chang, Z. Zhou, and T. Ristaniemi, “Reliable and Privacy-Preserving Task Recomposition for Crowdsensing in Vehicular Fog Computing,” IEEE 87th Vehicular Technology Conference (VTC Spring), pp. 1-6, June 2018.
H. Tian, F. Nan, C. C. Chang, Y. Huang, J. Lu, and Y. Du, “Privacy-Preserving Public Auditing for Secure Data Storage in Fog-to-Cloud Computing,” Journal of Network and Computer Applications, vol. 127, pp. 59-69, February 2019.
R. Almadhoun, M. Kadadha, M. Alhemeiri, M. Alshehhi, and K. Salah, “A User Authentication Scheme of IoT Devices Using Blockchain-Enabled Fog Nodes,” IEEE/ACS 15th International Conference on Computer Systems and Applications, pp. 1-8, October-November 2018.
M. Azeem, A. Ullah, H. Ashraf, N. Jhanjhi, M. Humayun, S. Aljahdali, et al., “FoG-Oriented Secure and Lightweight Data Aggregation in IoMT,” IEEE Access, vol. 9, pp. 111072-111082, 2021.
X. Liu, R. H. Deng, Y. Yang, H. N. Tran, and S. Zhong, “Hybrid Privacy-Preserving Clinical Decision Support System in Fog–Cloud Computing,” Future Generation Computer Systems, vol. 78, no. 2, pp. 825-837, January 2018.
A. Sudarsono, S. Huda, N. Fahmi, M. U. H. Al-Rasyid, and P. Kristalina, “Secure Data Exchange in Environmental Health Monitoring System Through Wireless Sensor Network,” International Journal of Engineering and Technology Innovation, vol. 6, no. 2, pp. 103-122, April 2016.
A. K. Chatamoni and R. N. Bhukya, “Lightweight Compressive Sensing for Joint Compression and Encryption of Sensor Data,” International Journal of Engineering and Technology Innovation, vol. 12, no. 2, pp. 167-181, February 2022.
B. A. Martin, F. Michaud, D. Banks, A. Mosenia, R. Zolfonoon, S. Irwan, et al., “OpenFog Security Requirements and Approaches,” IEEE Fog World Congress, pp. 1-6, October-November 2017.
M. Zobeiri and B. M. N. Maybodi, “Introducing Dynamic P-Box and S-Box Based on Modular Calculation and Key Encryption for Adding to Current Cryptographic Systems Against the Linear and Differential Cryptanalysis,” ARPN Journal of Engineering and Applied Sciences, vol. 12, no. 3, pp. 856-862, February 2017.
H. Alashwal, M. El Halaby, J. J. Crouse, A. Abdalla, and A. A. Moustafa, “The Application of Unsupervised Clustering Methods to Alzheimer's Disease,” Frontiers in Computational Neuroscience, vol. 13, pp. 92-100, May 2019.
“UCI Machine Learning Repository,” http://archive.ics.uci.edu/ml/datasets/mhealth+dataset, July 30, 2022.
Published
How to Cite
Issue
Section
License
Copyright Notice
Submission of a manuscript implies: that the work described has not been published before that it is not under consideration for publication elsewhere; that if and when the manuscript is accepted for publication. Authors can retain copyright in their articles with no restrictions. Also, author can post the final, peer-reviewed manuscript version (postprint) to any repository or website.

Since Jan. 01, 2019, IJETI will publish new articles with Creative Commons Attribution Non-Commercial License, under Creative Commons Attribution Non-Commercial 4.0 International (CC BY-NC 4.0) License.
The Creative Commons Attribution Non-Commercial (CC-BY-NC) License permits use, distribution and reproduction in any medium, provided the original work is properly cited and is not used for commercial purposes.







.jpg)


