Optimization of SM4 Encryption Algorithm for Power Metering Data Transmission
DOI:
https://doi.org/10.46604/ijeti.2023.12675Keywords:
SM4 cryptographic algorithm, hybrid algorithm optimization, S-box, nonlinearityAbstract
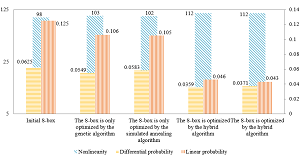
This study focuses on enhancing the security of the SM4 encryption algorithm for power metering data transmission by employing hybrid algorithms to optimize its substitution box (S-box). A multi-objective fitness function is constructed to evaluate the S-box structure, aiming to identify design solutions that satisfy differential probability, linear probability, and non-linearity balance. To achieve global optimization and local search for the S-box, a hybrid algorithm model that combines genetic algorithm and simulated annealing is introduced. This approach yields significant improvements in optimization effects and increased non-linearity. Experimental results demonstrate that the optimized S-box significantly reduces differential probability and linear probability while increasing non-linearity to 112. Furthermore, a comparison of the ciphertext entropy demonstrates enhanced encryption security with the optimized S-box. This research provides an effective method for improving the performance of the SM4 encryption algorithm.
References
R. Tiwari, P. Chithaluru, K. Kumar, M. Kumar, and T. Stephan, “A Cooperation Federated Forwarder Selection Technique for Maximizing Network Lifetime in Wireless Sensor Network,” Sādhanā, vol. 48, no. 3, article no. 135, 2023.
Sharmila, P. Kumar, S. Bhushan, M. Kumar, and M. Alazab, “Secure Key Management and Mutual Authentication Protocol for Wireless Sensor Network by Linking Edge Devices Using Hybrid Approach,” Wireless Personal Communications, vol. 130, no. 4, pp. 2935-2957, June 2023.
A. Banerjee, S. K. Gupta, P. Gupta, A. Sufian, A. Srivastava, and M. Kumar, “UAV-IoT Collaboration: Energy and Time-Saving Task Scheduling Scheme,” International Journal of Communication Systems, vol. 36, no. 14, article no. e5555, September 2023.
H. L. Liu, “Research on the Security Quantification Method of Data Transmission in Heterogeneous Super Super Density Networks,” Computer Simulation, vol. 38, no. 1, pp. 150-153, 2021.
Y. Liu, “Application of Data Encryption Technology in Network Security Transmission,” Cyberspace Security, vol. 14, no. 03, pp. 41-44, June 2023.
S. He, H. Li, and F. Li, “Optimization and Implementation of SM4 on FPGA,” Journal of Xi’an University of Electronic Science and Technology, vol. 48, no. 03, pp. 155-162, April 2021.
X. Zhang, K. Wei, and W. Jiang, “The Nonlinearity Optimization Algorithm of S-box Based on TD-ERCS Sequence,” Information Network Security, vol. 21, no. 01, pp. 10-18, January 2021.
M. F. Khan, K. Saleem, M. A. Alshara, and S. Bashir, “Multilevel Information Fusion for Cryptographic Substitution Box Construction Based on Inevitable Random Noise in Medical Imaging,” Scientific Reports, vol. 11, no. 1, article no. 14282, 2021.
M. F. Khan, K. Saleem, M. M. Hazzazi, M. Alotaibi, P. K. Shukla, M. Aqueel, et al., “Human Psychological Disorder towards Cryptography: True Random Number Generator from EEG of Schizophrenics and Its Application in Block Encryption’s Substitution Box,” Computational Intelligence and Neuroscience, vol. 2022, article no. 2532497, 2022.
A. H. Zahid, M. Ahmad, A. Alkhayyat, M. J. Arshad, M. M. U. Shaban, N. F. Soliman, et al., “Construction of Optimized Dynamic S-Boxes Based on a Cubic Modular Transform and the Sine Function,” IEEEAccess, vol. 9, pp. 131273-131285, 2021.
M. F. Khan, K. Saleem, M. Alotaibi, M. M. Hazzazi, E. Rehman, A. A. Abbasi, et al., “Construction and Optimization of TRNG Based Substitution Boxes for Block Encryption Algorithms,” https://doi.org/10.48550/arXiv.2206.09424, June 19, 2022.
L. Zhang, L. He, and B. Yu, “Design and Analysis of Large-Scale S-Boxes with SPS Structure,” Journal on Communications, vol. 44, no. 2, pp. 27-40, February 2023.
S. A. Susan T and N. Balasubramanian, “A Hybrid Metaheuristic Algorithm for Stop Point Selection in Wireless Rechargeable Sensor Network,” International Journal of Engineering and Technology Innovation, vol. 13, no. 4, pp. 296-312, October 2023.
A. J. P. Delima, “An Enhanced K-Nearest Neighbor Predictive Model through Metaheuristic Optimization,” International Journal of Engineering and Technology Innovation, vol. 10, no. 4, pp. 280-292, September 2020.
J. Zhao, “Research on Security Protection Strategy for Data Transmission Based on Internet of Things,” M.S. dissertation, Department Communications Engineering, Jilin University, Changchun, May 2020.
S. Yang, “Research on Cryptographic Algorithms Based on Chaotic Systems and Optimized S-Boxes,” M.S. dissertation, Harbin Institute of Technology, Harbin, June 2022.
Y. Wang, M. Wang, and J. Gong, “Optimal Design Method of 8x8 S-box Based on Multi-objective Genetic Algorithm,” Journal of Southwest Jiaotong University, pp. 1-10, June 2022.
L. Wang, “Optimized Design of Chaotic S-Box and Its Application in Image Encryption,” M.S. dissertation, Changsha University of Science and Technology, Changsha, June 2021.
Zhengquan Li, Yawen Lu, Ruiqing Qin, Lirong Tan, and Bin Gu, An S-Box Design Method Based on Hyperchaotic Systems with Genetic Particle Swarm Algorithm, Chinese Patent, CN202210563082.5, August 2022. (In Chinese)
X. Tong, D. Zhu, and M. Zhang, An S-Box Optimization Method Based on Improved Genetic Algorithm, Chinese Patent, CN202010571146.7, October 2020.
Y. Si, H. Liu, and M. Zhao, “Constructing Keyed Strong S-Box with Higher Nonlinearity Based on 2D Hyper Chaotic Map and Algebraic Operation,” Integration, vol. 88, pp. 269-277, January 2023.
X. Liu, X. Tong, Z. Wang, and M. Zhang, “Efficient High Nonlinearity S-Box Generating Algorithm Based on Third-Order Nonlinear Digital Filter,” Chaos, Solitons & Fractals, vol. 150, article no. 111109, September 2021.
Published
How to Cite
Issue
Section
License
Copyright (c) 2023 Yi-Ming Zhang, Jia Xu, Yi-Tao Zhao, Qing-Chan Liu, Qiu-Hao Gong

This work is licensed under a Creative Commons Attribution-NonCommercial 4.0 International License.
Copyright Notice
Submission of a manuscript implies: that the work described has not been published before that it is not under consideration for publication elsewhere; that if and when the manuscript is accepted for publication. Authors can retain copyright in their articles with no restrictions. Also, author can post the final, peer-reviewed manuscript version (postprint) to any repository or website.

Since Jan. 01, 2019, IJETI will publish new articles with Creative Commons Attribution Non-Commercial License, under Creative Commons Attribution Non-Commercial 4.0 International (CC BY-NC 4.0) License.
The Creative Commons Attribution Non-Commercial (CC-BY-NC) License permits use, distribution and reproduction in any medium, provided the original work is properly cited and is not used for commercial purposes.







.jpg)


